Shorten. Secure. Control. Access-Smart.
Turn any link into a secure, access-aware smart URL with IP/DNS control, AI analytics, and privacy-first tracking.


Why IP/DNS Smart Links?
Traditional shorteners create public links open to everyone, exposing internal resources and lacking network or geographic control. Security teams then build complex authentication systems that hinder access and break tracking.
Modern teams face security gaps, bot traffic, and zero control over who reaches sensitive content.
Open Access Risk
No Restrictions
No Device Insights
Misdirected
Exposed Resources
Complex setup for Device targeting.
Limited visibility beyond basic clicks
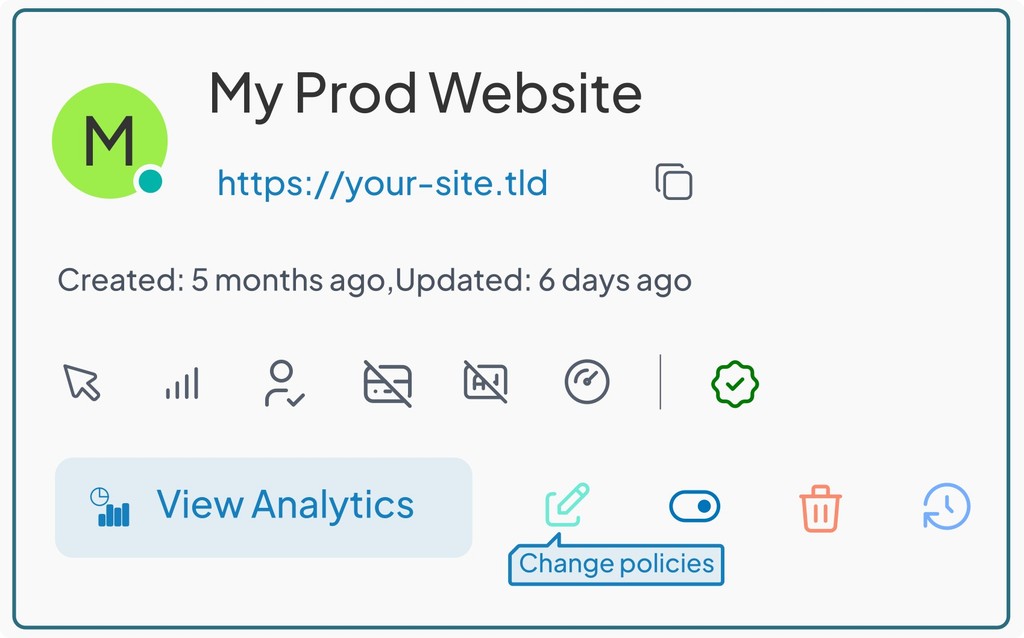
IP/DNS Restricted Smart Redirect Short URLs simplify secure link management. A single link validates each user’s IP or DNS, granting or blocking access automatically, while AI-powered, cookie-less analytics provide real-time insights into access patterns, geography, and security events with full privacy.
Instant Secure Links
Auto Access Rules
Real-Time Control
Unified Analytics
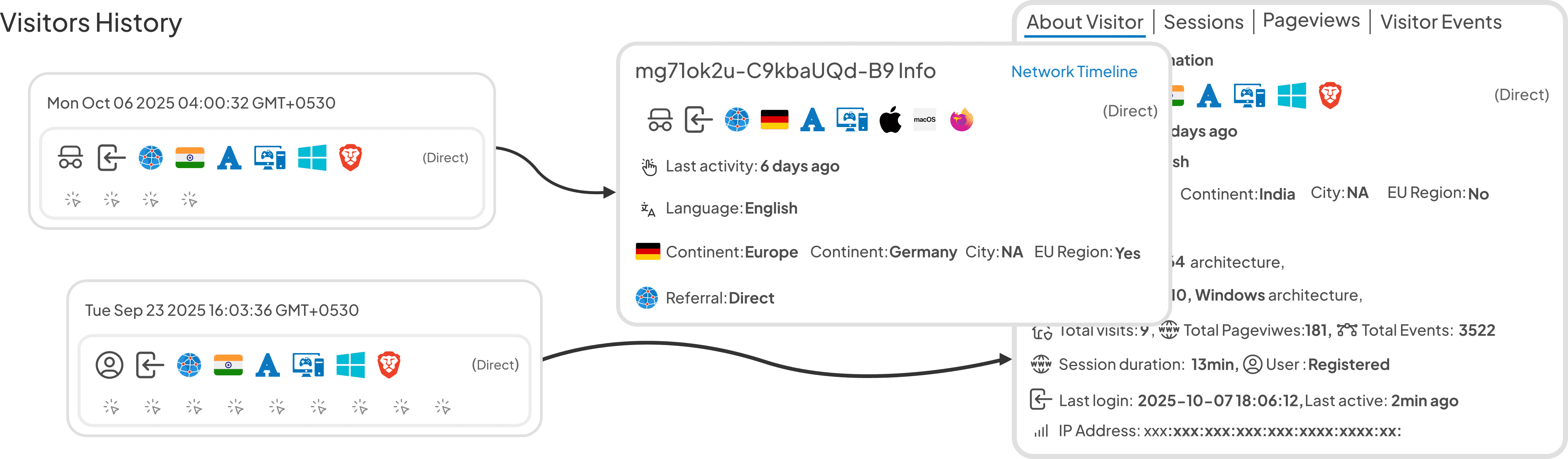
Device & Browser Tracking
Regional Campaign Analytics
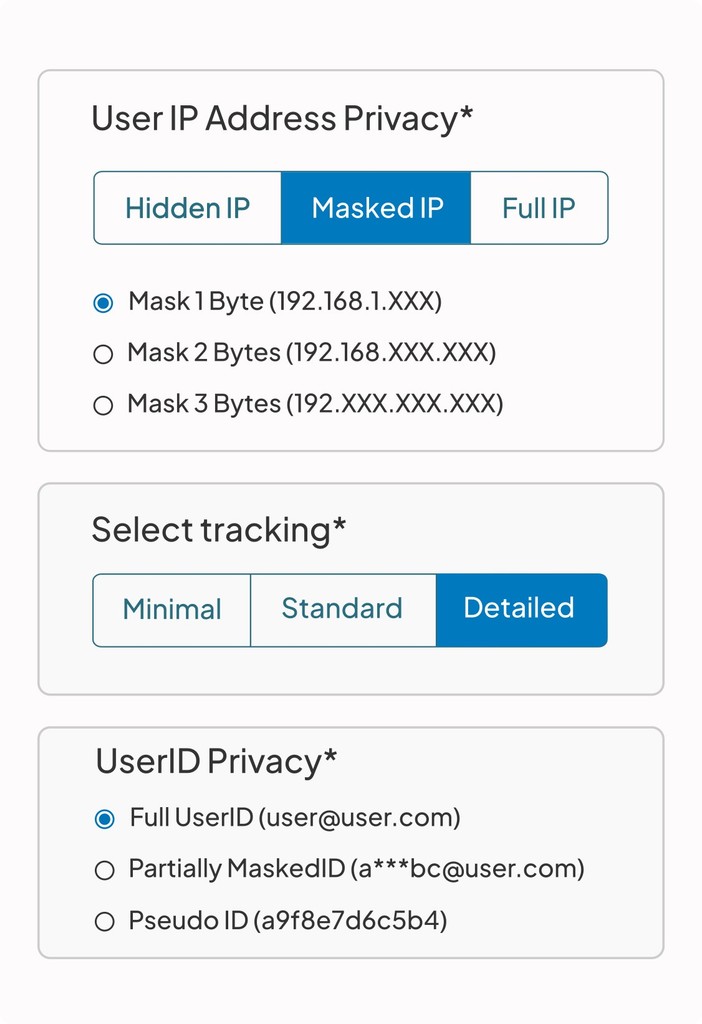
Cookie-Less Privacy
AI-Powered Reports & Charts
Instant Updates
How It Works
Instant security-intelligent URL shortening, automatic IP/DNS validation, AI-powered analytics, and full control—all from one platform.
01
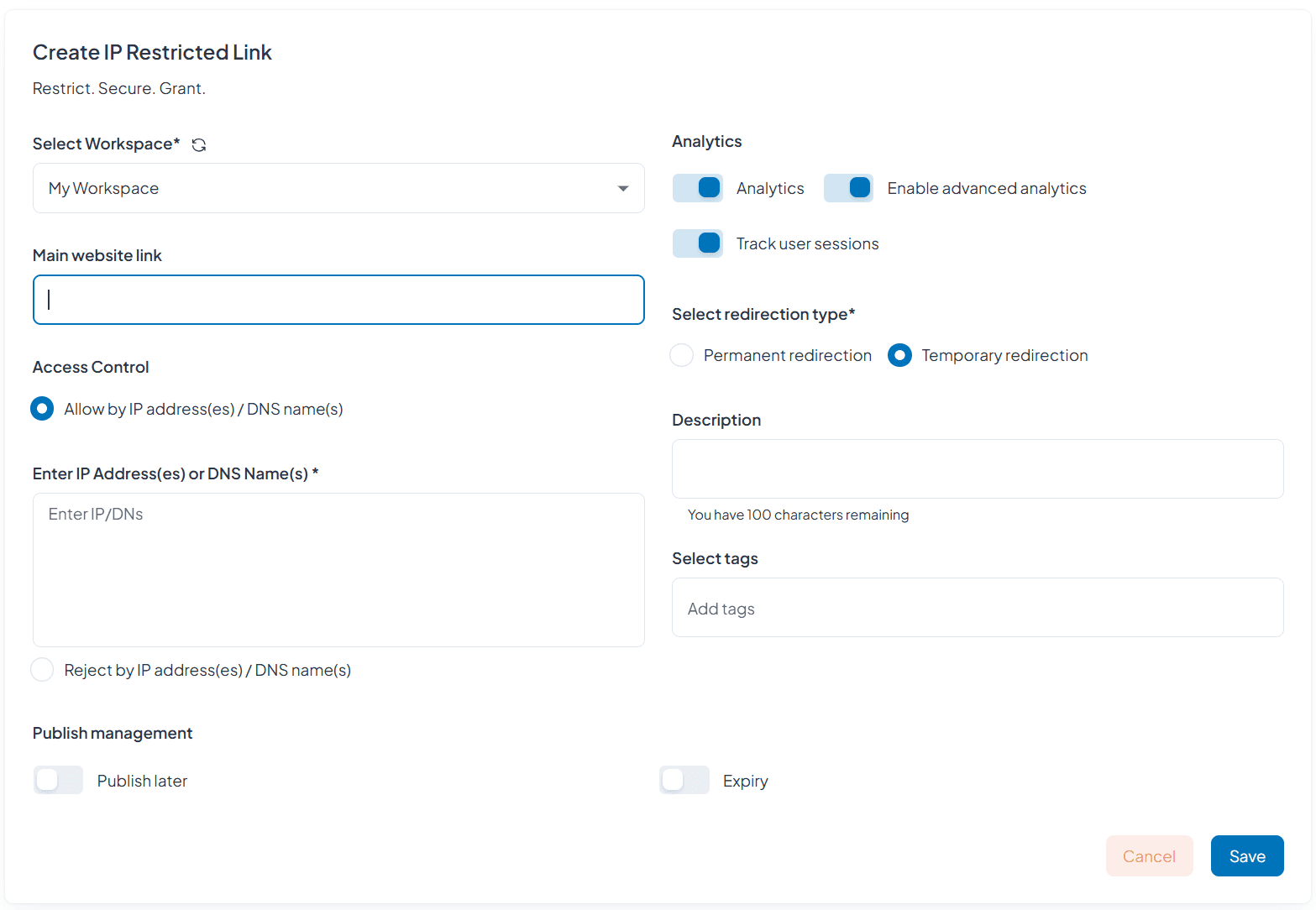
Create Your Smart IP/DNS Controlled Short Link
Set Your Access Rules and Generate Instantly
Enter your destination URL (for authorized access)
Configure access control rules:
Allow List: Whitelist specific IPs, IP ranges, countries, or DNS
Block List: Blacklist specific IPs, IP ranges, countries, or DNS
DNS-Based Control: Allow/block based on DNS resolution
Set redirection URLs
Choose your analytics depth:
Basic: Access tracking with allow/deny logging
Advanced: Full security analytics and threat intelligence
Configure session tracking preferences
Set optional expiration dates
Generate your single secured short URL
02
Share Your Smart Link
Share Your Smart Source Link
One Link. Every Channel. Complete Visibility.
Copy your single shortened URL instantly
Share across social, search, email, ads—one link for all sources
Works across all platforms and referrers
Automatic traffic source detection
Intelligent redirect to appropriate channel-optimized destination
Fallback to default if source not configured
No additional technical setup or UTM complexity required
03
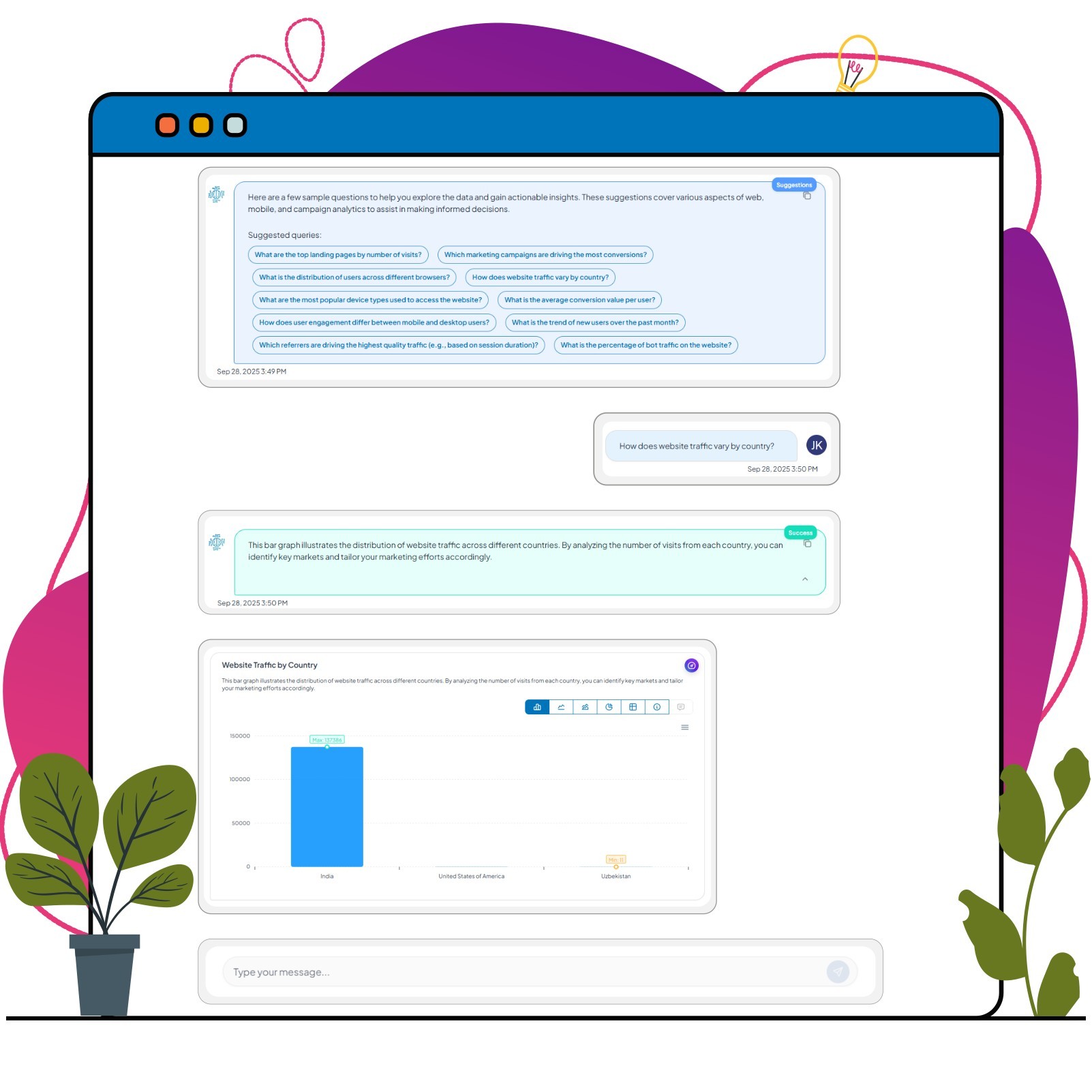
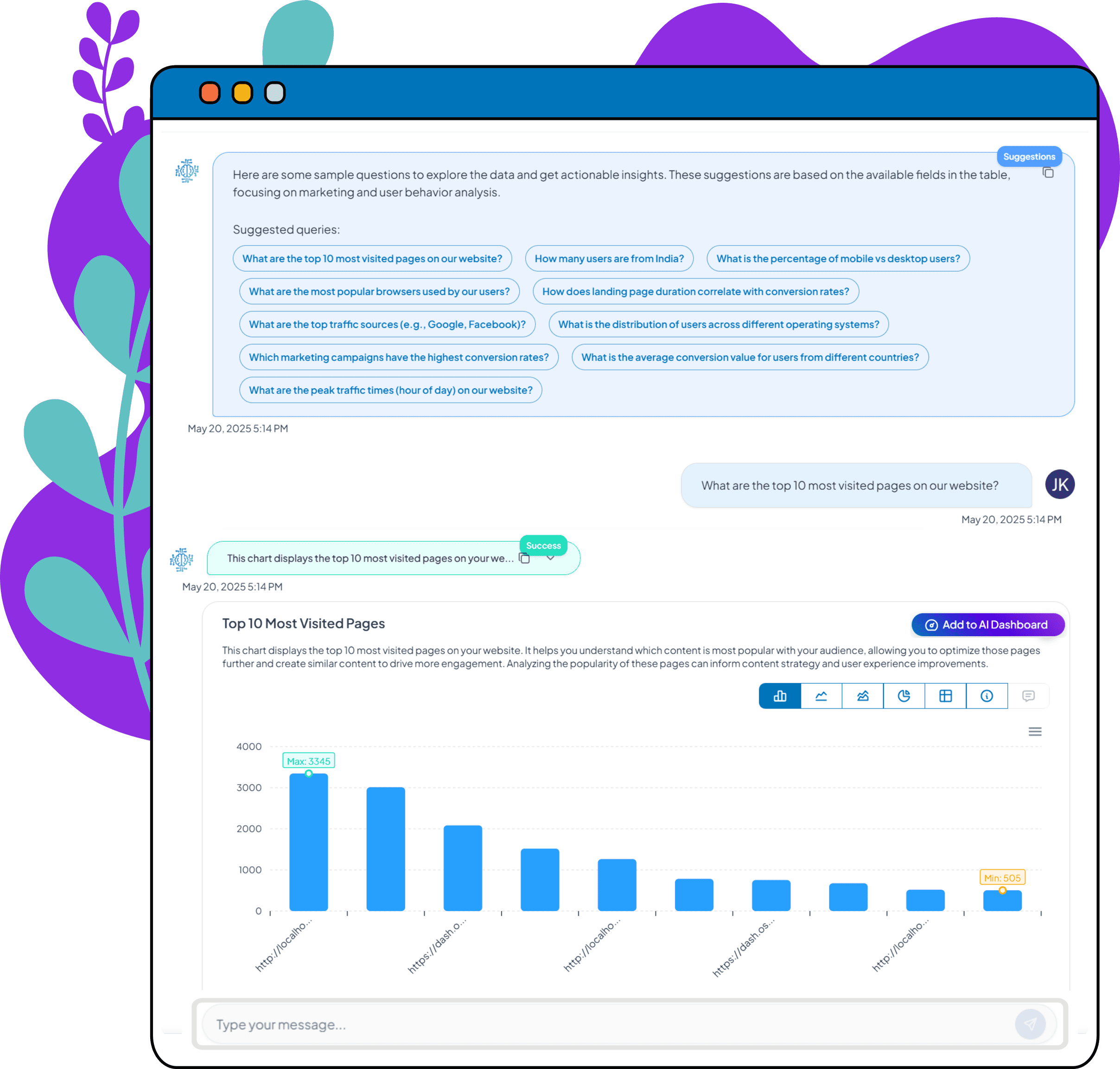
Unlock AI-Powered Source Insights
Immediate Intelligence Across All Access Patterns
Access your unified dashboard immediately after first access attempt
Explore AI-generated reports on allowed vs blocked traffic
Real-time monitoring of access patterns and security events
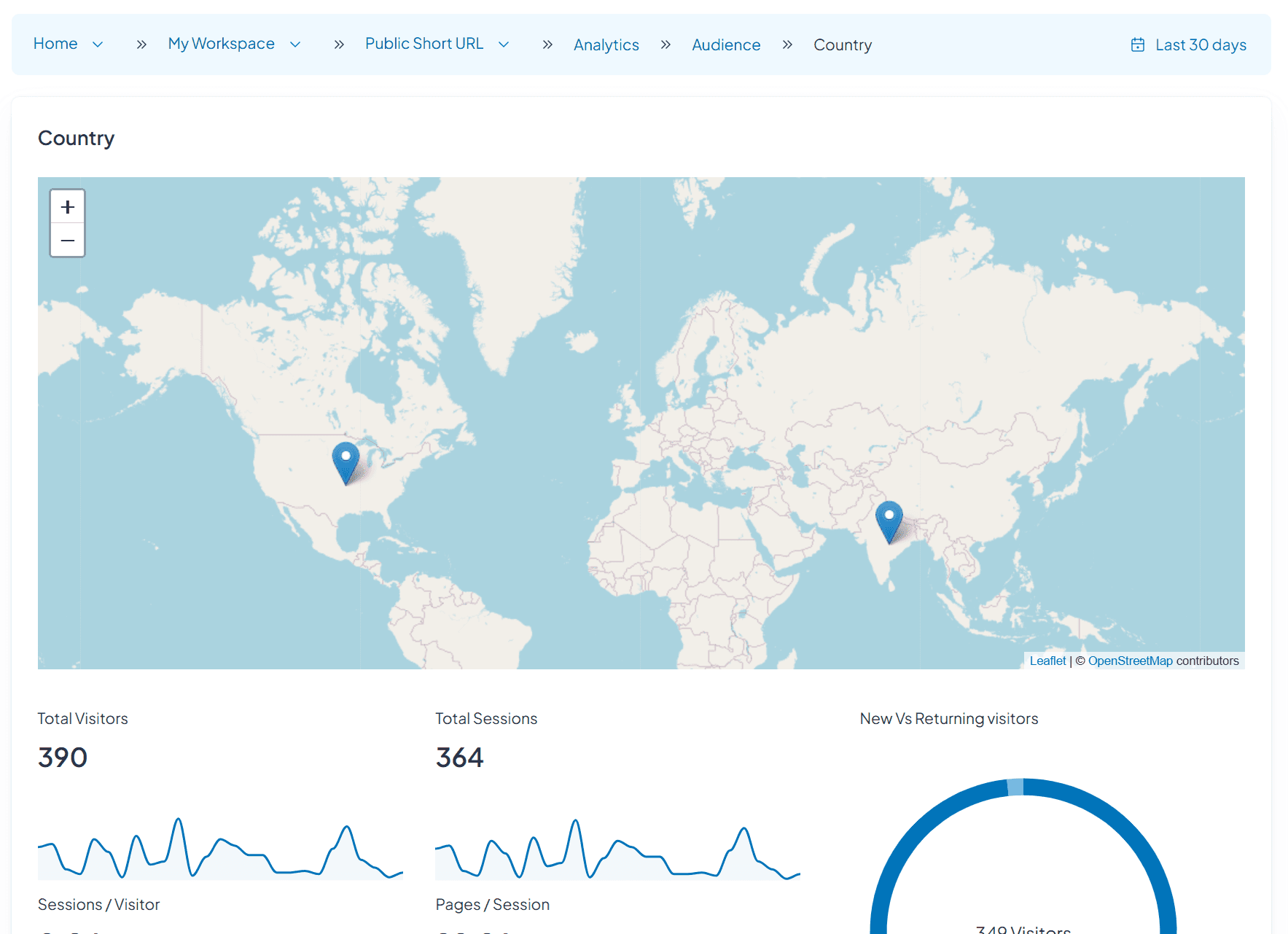
See which geographic regions attempt access
Drill down into legitimate traffic vs unauthorized attempts
Compare access patterns across rules and regions
Export security data or integrate insights with your tools
☆
Immediate Source-Optimized Value
Start gaining security insights the moment your first link goes live. IP/DNS Restricted Smart Redirect activates real-time access analytics instantly—no setup, no configuration, no waiting. See access attempts, blocked traffic, geographic patterns, and security events within seconds of sharing your secured link.
Core Features
Your secure content deserves analytics beyond clicks. Get full visibility into access patterns, security events, and real-time threat detection.
View All Features
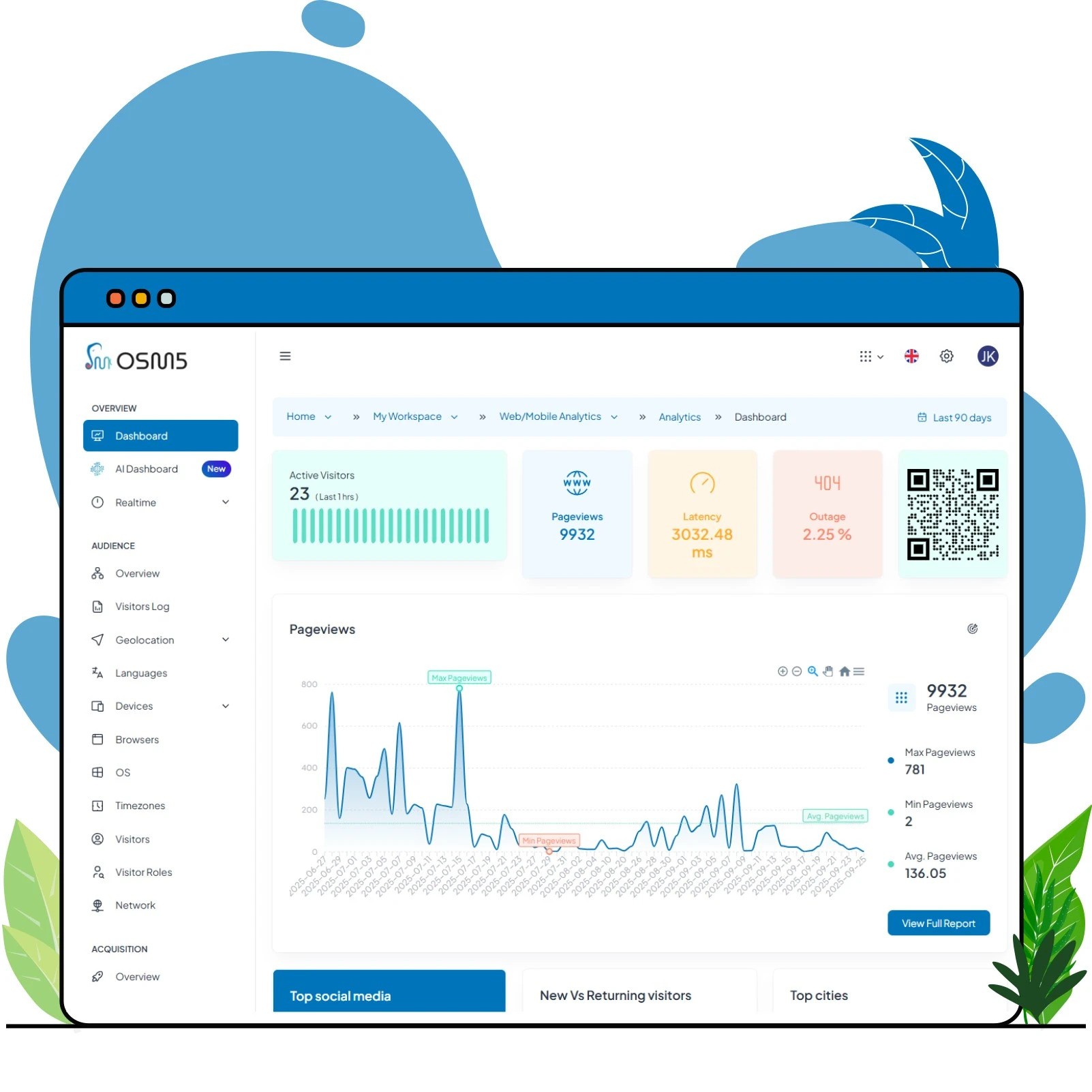
Explore every dimension of your IP-restricted short links with AI-powered dashboards. From access control insights to real-time performance by region or network, uncover how secure, targeted experiences drive your growth.
Complete Control. Infinite Flexibility. Access-Optimized.
Analytics Dashboard Preview
Your security needs evolve. Your access-controlled links should too. Change anything, anytime—even after your links are live and shared.
Use Cases
Stop exposing resources to everyone. Start measuring with access control intelligence.
Stop Guessing. Start Securing by Access.
Every access-controlled link becomes a security intelligence source that drives smarter policies, better protection, and measurable security improvements.